Hybrid Threats - Concept and Recognition Guide
This is not an easy to digest book and doesn’t offer a modeler a lot of references, resources, or inspiration for modeling. Having said that, author Michael Fredholm von Essen, did an admirable job of defining a nebulous threat that is hard to recognize, much less counter. From his introduction,
This book describes hybrid threats to national security, and how to deploy them as weapons against an adversary. Designed to be difficult to detect or attribute, hybrid threats constitute a twenty-first-century concept which enables, often with the help of advanced technology, the use of military and non-military means under conditions of plausible deniability.
The end of the Cold War was marked by the dissolution of the Soviet Union in 1991. A period of anticipated “peace dividend” and the world would welcome in a new period of “liberal democracy and free-market capitalism of the Western style to rest of the planet signified the final stage of humanity’s sociocultural evolution and would become the final form of human government”, according to American political scientist Francis Fukuyama. As we now know, the world has changed, but not in the way described here. Rather,
The world had not seen the end of history, after all. Instead, new poles of power emerged to threaten the Western-dominated world order. While the perceived threats often were quite similar, or even identical, to those in the past, there was a qualitative difference. This was largely the effect of the two major trends of the 1990s. Globalization, and yet more importantly, digitalization had changed the world since 1991. Together, these two trends caused a dramatic increase in connectivity. Henceforth, trends and opinions rapidly spanned the globe, which provided vastly enhanced leverage for opportunistic action by hostile actors.
You can already see that this book is going to be an academic tone about a serious national threat. It is a good book, but not for most of our model builders.
This 72-page book is part of Helion & Company’s @War Series. Hybrid Threats - Concept and Recognition Guide (Helion No. HEL2082) is outlined in the familiar @War format with 72 pages with 35 color photographs, four black and white photographs, 8 color profiles, 1 color map, and six tables. The book is composed of the following sections:
- Abbreviations and Acronyms
- Introduction
- The Concept
- New Vulnerabilities
- Asymmetric Warfare
- Hybrid Warfare
- Indirect and Asymmetric Operations
- Hybrid Threats
- The EU Intelligence and Situation Centre (EU-INTCEN)
- The European Centre of Excellence for Countering Hybrid Threats (Hybrid CoE)
- Proxies
- Recognition Guide
- Case Studies
- State Power
- Cyber Power
- Privatized Power
- People’s Power
- Terrorist Power
- Real Economic Power
- Financial Power
- Scientific & Technological Power
- Media Power
- Non-State Actors
- Acting as States
- Organized Crime
- The Afghan Taliban
- Countering Hybrid Threats
- The Concept
- Bibliography
- End Notes
- About the Author
The bulk of this book focuses on second and third chapters, Recognition Guide and Non-State Actors, respectively. The Recognition Guide chapter provides case studies that are defined by the chapter’s subtitles of the different kinds of power outlined above. The case studies include:
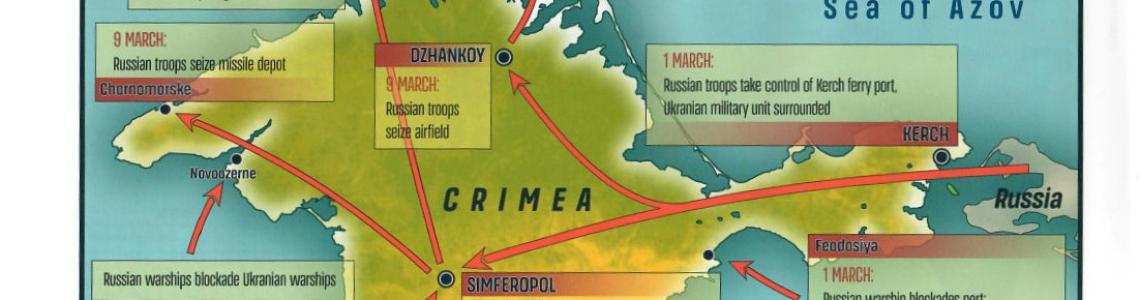
- Case Study: Little Green Men of Crimea, February-March 2014
- Case Study: Mabna Institute, Iranian Hackers-for-Hire, 2013-2018
- Case Study: D-Company, Indian Smuggles-for-Hire, 1986-2024
- Case Study: Free Syrian Army, Syrian Insurgents on a Retainer, 2011-2012
- Case Study: Chatayev Group of the Caucasus Emirate, Chechen Jihadists-for-Hire, 2012
- Case Study: Nord Stream AG, International Consortium for Natural Gas Supplies, 2005-2009
- Case Study: SWIFT, Unwilling Belgian Society for the Imposition of Sanctions, 2018
- Case Study: Afghan Taliban, Pashtun Proxy with Own Agenda, 1994-2020
- Case Study: International University Exchange Fund, Well-Endowed Nordic Proxy, 1969-1980
- Case Study: MINERVA, Swiss Manufacturer of Backdoors, 1970-1995
- Case Study: Patriot and Blitz, Indian Purveyors of Active Measures, 1980-1982
- Case Study: Ghostwriter, Composer of Fabricated Content, 2017-2022
- Case Study: CENTCOM and Operation Earnest Voice, Bot Operator and Fabricator of Fake Online Personas
The Non-State Actors chapter is a fascinating overview of the Afghan Taliban, as outlined here:
- Background
- The Taliban Movement in the 1990s
- The Post-2001 Taliban Movement
- Hybrid Warfare and Hybrid Threats
- The Domestic Theatre: Hybrid Warfare
- Military Power Projection against ISAF and ANSF
- Terrorist Power Projection against the ISAF and ANSF
- Terrorist Power Projection against the Afghan Population
- Media Power Projection against the Afghan Population
- Power Projection through Organized Crime
- The International Theater: Hybrid Threats
- Diplomatic Power Projection against the ISAF Member States
- Diplomatic Power Projection against the Worldwide Muslim Community
- Media Power Projection against the ISAF Member States and the Worldwide Muslim Community
- Terrorist Power Projection against ISAF Soldiers’ Family Members
- Terrorist Power Projection in the Form of Attacks Abroad
- Concluding Remarks on the Afghan Taliban’s Hybrid Threats Power
It is obvious that this book is a passion for the author, who is a historian and former military analyst. His background shows throughout this book, which is not easy to digest, but has incredible information for anyone who wants to learn more about hybrid threats on the modern stage. Was the Amazon Web Service (AWS) outage on Monday, 20 October 2025 a glitch, or a hybrid attack on a third of the world’s internet?
Profuse thanks to Casemate and IPMS-USA for providing the review sample.










Comments
Add new comment
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
Similar Reviews